OWASP ZAP integration – Security Compliance with AWS Config, AWS Security Hub, and Automated Remediation
OWASP ZAP integration
As a free open source SAST solution, OWASP ZAP can be used to actively test web applications for vulnerabilities during runtime, offering an effective complement to SAST. This dynamic assessment is crucial for uncovering runtime issues such as authentication and session management flaws, Cross-Site Scripting (XSS), and SQL injection, among other vulnerabilities. The tool’s ability to simulate real-world attack scenarios gives a realistic assessment of how applications might fare against actual security threats. This includes performing authenticated scans to test both public and private aspects of applications.
When embedded in CI/CD pipelines, OWASP ZAP automates security testing as part of the deployment process. This integration ensures that each new release undergoes thorough security assessments, thereby identifying and addressing vulnerabilities at the build stage in a test environment. The tool’s customizable scanning capabilities allow teams to tailor security tests to their specific application architecture and security needs, ensuring effectiveness across different application types.
OWASP ZAP’s integration also includes generating detailed reports after each scan. These reports are crucial for providing developers and security teams with actionable insights into potential security risks. Immediate feedback facilitates prompt remediation efforts, enhancing the overall security posture of the application.
As we move forward, we will integrate the insights gained from these third-party tools with the centralized capabilities of AWS Security Hub.
Tooling integration with Security Hub
Integrating Security Hub into CI/CD pipelines enhances the security management process by providing a unified platform that aggregates, organizes, and prioritizes security alerts from various AWS services and third-party tools. Thanks to the AWS security finding format (ASFF), Security Hub ensures that all security findings are standardized, making it simpler to monitor and address potential issues identified by different tools, be it SAST, DAST, or SCA. This standardization is key in allowing for effective cross-tool data analysis and reporting.
Teams can set up custom security alerts in Security Hub tailored to their specific needs and risk profiles, enabling rapid response to critical issues detected by the integrated security tools. Additionally, the integration streamlines the process of managing and remediating security findings. Teams can use Lambda functions or other automated mechanisms for quick and efficient resolution of security issues.
The following diagram (Figure 12.4) illustrates how Security Hub can be integrated with both AWS native and third-party tools attached to various stages of the CI/CD pipeline:
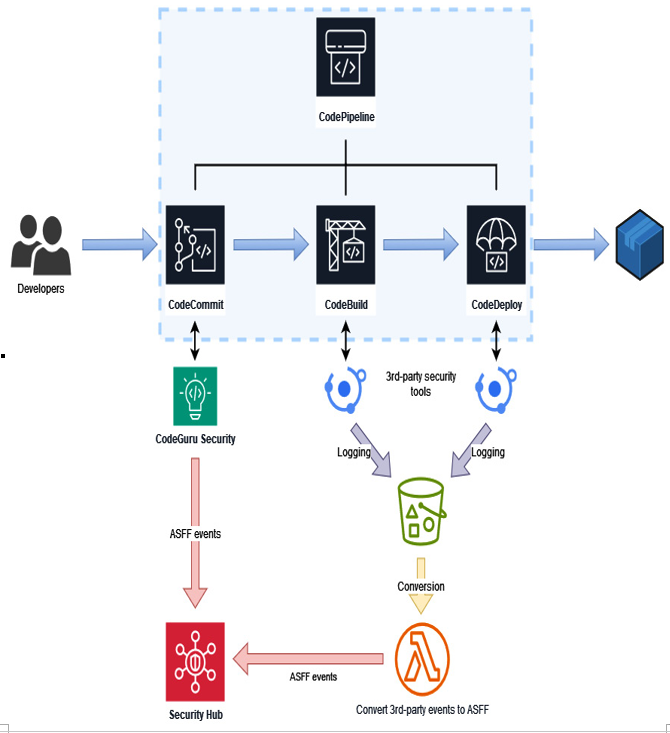
Figure 12.4 – Security Hub integration into the CI/CD pipeline
Next, let’s turn our attention from Security Hub to best practices that are key to successfully integrating security tools in the CI/CD landscape.